EU member states should have transposed by 17 October 2024 the Directive on measures for a high common level of cybersecurity across the EU (NIS2). However, most EU member states did not meet the transposition deadline. Thus far, only Belgium, Croatia, Hungary, Italy, Latvia, and Lithuania have adopted national legislation to transpose the directive.
The NIS2 repealed and replaced on 18 October 2024 the former NIS Directive, and also repealed articles 40 and 41 of the European Electronic Communications Code (EECC).
In several member states, including for example France, Germany, the Netherlands and Sweden, the draft laws transposing the directive were not yet adopted into law.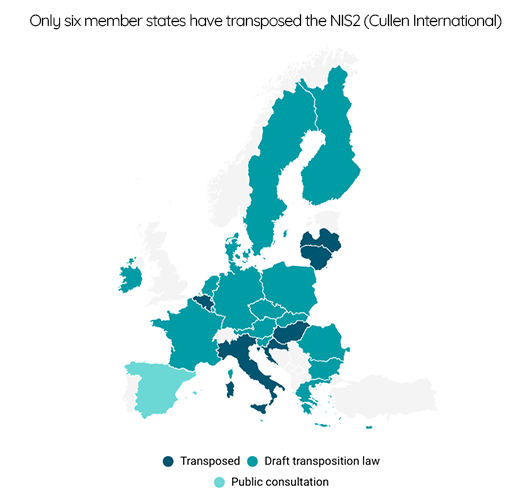
If a member state does not transpose EU legislation by the deadline, the European Commission may launch an infringement procedure and ultimately refer a member state to the Court of Justice of the EU (CJEU).
The NIS2 Directive imposes baseline cybersecurity risk-management requirements and incident reporting obligations to entities operating in EU critical sectors (e.g. energy, telecoms, cloud computing). Additionally, certain digital entities, for example cloud providers, data centres, managed security service providers (MSSPs), are subject to EU harmonised security obligations under a Commission implementing regulation. The latter details:
- the cybersecurity risk management measures that these entities are required to adopt; and
- the cases in which an incident should be considered significant and notified to the national competent authority.
The Commission adopted the implementing regulation on 17 October 2024. According to the Commission’s press release, the implementing regulation will be published in the Official Journal of the EU “in due course” and enter into force twenty days thereafter.
A draft implementing regulation was open to feedback until 25 July 2024. Following the consultation, the final text of the regulation introduced some changes compared to the draft, in particular related to the thresholds to report incidents. For example, an incident will be considered significant and notified where:
- It can cause financial loss for the entity concerned exceeding €500,000 (instead of €100,000) or 5% of the entity’s total annual turnover in the preceding financial year (whichever is lower). The entity should consider all costs related to the incident, e.g. staff expenses, compensating costs for customers.
- The services of cloud providers and MSSPs should be unavailable for more than 30 minutes (instead of the originally proposed 10 minutes) for the incident to be reported as significant.
The NIS2 Directive requires that only significant incidents are notified to the national competent authorities following a multi-step process. The initial notification should be submitted within 24 hours, followed by a second one within 72 hours after having become aware of a significant incident. A final report providing additional information on the breach should be submitted in one month.
For more information on Cullen's NIS2 transposition benchmark and complete NIS2 report coverage, please click on “Access the full content” - or on “Request Access”, in case you are not subscribed to our European Digital Economy service.
more news
20 February 26
Revised Cybersecurity Act (CSA2) - Changes to the EU cybersecurity certification framework
Cullen International published an analysis of the proposed changes to the EU cybersecurity certification framework under the draft Cybersecurity Act 2 (CSA2) delivered by the European Commission on 20 January 2026.
19 February 26
Upper 6 GHz band: EU member states wait for EU-level decisions
Cullen International has been monitoring regulation of the upper 6 GHz band at the European level and now also benchmarks regulation at the national level in Europe.
18 February 26
The DNA explained: more EU guidance to protect end users against fraud
Cullen International is issuing a series of analyses on different aspects of the Digital Networks Act (DNA) proposal. This report covers end-user rights.